Company Profile
Fortune 1000 Global Manufacturing Company with 10,000+ employees
Problem
Company has been hit with malware and ransomware in the past. They have multiple cyber security tools in place, however are worried about existing endpoint protections and would like the ability to search for both SHA-1 hash values as well as snippets of code identified by IT staff as potentially malicious.
Solution
Heureka's endpoint service automatically creates both MD5 and SHA1 hashes for each file that is indexed. Interrogate has a built-in hash value search along with known hash-based Indicators of Compromise. A single scan across all endpoints for all IOC's will indicate whether or not an endpoint may have compromised software. Additionally, with keyword searching it is possible to run a code snippet search to discover endpoints with plain-text code.
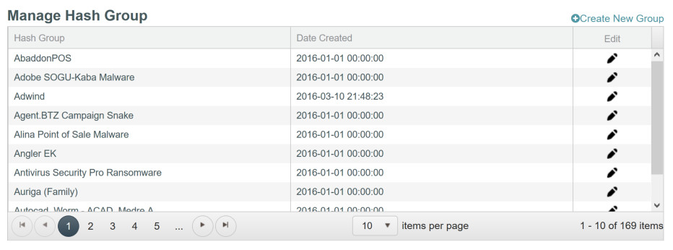
Interrogate Workflow #1 for Hash-based Indicators of Compromise (User Defined)
Interrogate comes pre-seeded with over 160 known hash-based Indicators of Compromise. These IOC's can be found in the hash group area when setting up the search criteria. Additionally, Heureka Software publishes updates to known IOC's on the main help page. Newly published IOC's allow you to create new groups or add new information (labeled as SUPPLEMENTAL) to pre-existing hash groups.
You can easily scan all endpoints for any or all of the hash groups built into the system.
Search
Interrogate's search feature allows you to define both endpoints and specific file names or extensions to search for.
- Create a Job and Search in Interrogate.
- Select the desired endpoints you would like to search.
- For this use case, we are looking for all hash groups currently in the system. Click "Select All" on the File > Hash area.
- Select "Search" and input name.
Analyze
If the endpoint(s) begin to stream results back to your search result page, you will see file-level information such as File Name, Risk Score, Tags, File Path, etc, in the Grid Results area. When scanning for IOC's, the indication of a returned file may indicate an infected endpoint. Action should be taken on the endpoint.
Take Action
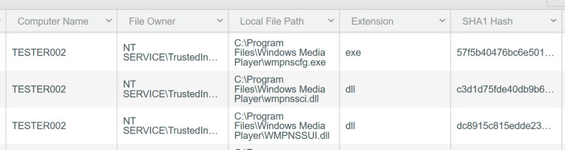
A returned file from the IOC hash groups may be an indication that you could have a potentially infected computer(s). Looking at the computer name, file owner and local file path as well as extension will help you or you IT department track down the exact location of the potentially infected file.
Interrogate Workflow #2 for Plain-text code snippet (User Defined)
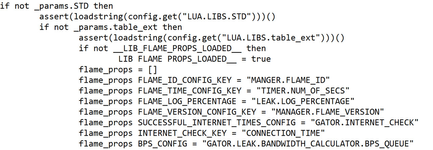
Some maleware may appear in plain-text and thus is searchable using Interrogate. The top example at the right is a snippet of code written in LUA as part of the Flame espionage worm. As you can see, the code is in plain language and as such is text searchable using Interrogate.
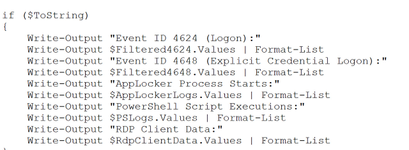
The bottom example is script taken from a .ps1 file (Microsoft Powersploit Powershell script) commonly used by penetration testers during assessment. This same script can be valuable to hackers who are attempting to pull machine intelligence from an endpoint.
In either case, you will be using Interrogate's Keyword functionality to look for code snippets.
Search
Interrogate's search feature allows you to define both endpoints and specific keywords for searching.
- Create a Job and Search in Interrogate.
- Select the desired endpoints you would like to search.
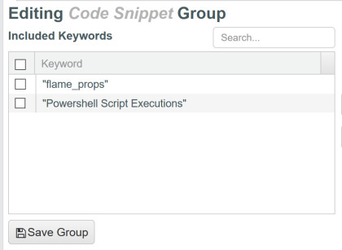
- For this use case you will be using keywords in order to search for code snippets. See the example at the bottom right showing keyword group setup.
- Select "Search" and input name.
Analyze
If the endpoint(s) begin to stream results back to your search result page, you will see file-level information such as File Name, Risk Score, Tags, File Path, etc, in the Grid Results area. If you discover some of the code you were searching for, it may indicate malicious activity at the endpoint level. See "Take Action" listed below.
Take Action
A returned file from code snippet keywords may be an indication that you could have malicious code on an endpoint. Looking at the computer name, file owner and local file path as well as extension will help you or you IT department track down the exact location of the potentially infected file.
Example of LUA code snippet for Flame malware
Example of PowerSploit script in plain language
Example "Code Snippet" keyword group created for searching endpoints